DeviantArt user: Tincho555
Researchers have uncovered a seven-year-old malware operation that combines advanced cryptographic attacks, zero-day exploits, and well-developed keyloggers to target elite executives staying in luxury hotels during business trips.
The attackers behind “DarkHotel,” as the advanced persistent threat has been dubbed, appear to know in advance when a targeted exec will check in and check out of a hotel. Victims are infected through a variety of methods, including bogus software updates for Adobe Flash, Google Toolbar, or other trusted software that are presented when the exec uses the hotel’s Wi-Fi or wired Internet access. In many cases, the attack code is signed with a trusted digital certificate that the attackers were able to clone by factoring the underlying 512-bit private key. While factoring weak 512-bit keys has been practical for several years, the crypto attack nonetheless is an “advanced” capability, particularly a few years ago. Taken together, the characteristics are an indication the operators have some sophistication, said researchers from Kaspersky Lab, the Russia-based security firm that disclosed the campaign.
“The fact that most of the time the victims are top executives indicates the attackers have knowledge of their victims whereabouts, including name and place of stay,” the researchers wrote in a report published Monday. “This paints a dark, dangerous web in which unsuspecting travelers can easily fall. While the exact reason why some hotels function as an attacker vector are unknown, certain suspicions exist, indicating possibly a much larger compromise. We are still investigating this aspect of the operation and will publish more information in the future.”
Kaspersky researchers observed DarkHotel malware spreading in several undisclosed hotel networks when people connected to Wi-Fi were prompted to install counterfeit software updates. In other cases, targets are infected through spearphishing messages, some of which include attack code exploiting previously unknown vulnerabilities in Flash, Internet Explorer, or other types of software. Once infected by DarkHotel, computers will install various keyloggers or other forms of malware that are tailored to specific victims. The malware monitors passwords, communications, and system information on infected machines and periodically sends the data in encrypted form to servers controlled by the attackers. One of the things that makes the campaign unusual is its use of luxury hotel networks as a watering hole of sorts to target and infect high-value executives. The report stated:
In this case, the Darkhotel attackers wait for their victim to connect to the Internet over the hotel Wi-Fi or the cable in their room. There is a very strong likelihood the targets will connect over these resources, and the attackers rely on that likelihood, much like at a watering hole. But the attackers also maintain truly precise targeting information over the victim’s visit, much like they would know a victim’s e-mail address and content interests in a spearphishing attack. While setting up the attack, the Darkhotel attackers knew the target’s expected arrival and departure times, room number, and full name, among other data. This data enables the attackers to present the malicious iframe precisely to that individual target. So, here we have yet another unique characteristic of this attacker—they employ a loosely certain but highly precise offensive approach.
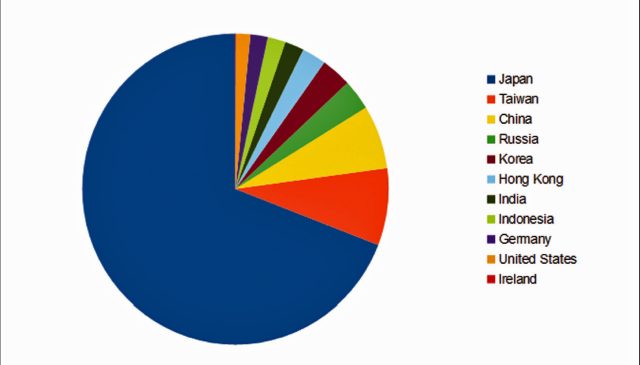
DarkHotel malware was also seeded to bittorrent feeds, where it was downloaded more than 30,000 times in less than six months. Kaspersky-owned network sensors have detected “thousands” of DarkHotel infections, mostly from the bittorrent feeds. Japan, Taiwan, China, Russia, and Korea were the five countries most affected by the malware.
Much of the malware is or was cryptographically signed with digital certificates belonging to a trusted third party. All of the underlying private keys of the cloned certificates were generated using 512-bit md5 keys. The ability of attackers to factor the weak keys for use in such malware attacks has long been known, as advisories issued from Fox-IT, Microsoft, Mozilla, and Entrust warned in 2011. All the cloned keys have expired or been revoked. Signing code with trusted certificates helps eliminate warning messages that may be presented during installation.
“All related cases of signed Darkhotel malware share the same Root Certificate Authority and Intermediate Certificate Authority that issued certificates with weak md5 keys (RSA 512 bits),” Monday’s Kaspersky report stated. “We are confident that our Darkhotel threat actor fraudulently duplicated these certificates to sign its malware. These keys were not stolen.”
More recently, DarkHotel operators have stolen third-party certificates to sign their malware.
Some of the DarkHotel malware samples date back to 2007. One file includes a keylogger designed to resemble a legitimate low-level Microsoft system device. Other components include a small downloader, an information stealer, a dropper and selfinjector, and a “selective infector” that infects executable files with an old-fashioned virus.
via arstechnica.com



