EXPLOIT.RTF.RTFEXP.AC
Platform: Win32
Type: Exploit
Size: 1410681 bytes
File type: rtf
MD5: 93d0222c8c7b57d38931cfd712523c67
SHA1: 94b802273340f406d5bfda7812330d15eb8dcdeb
Aliases : Red October RTF, Exploit.Win32.CVE-2012-0158
Summary
This Exploit uses a vulnerability in Microsoft Windows Common Control Library (MSCOMCTL.OCX) ActiveX (CVE-2012-0158, MS12-027 ) to execute an arbitrary code on a target computer.
It uses a malicious RTF to embed the specially crafted MSComctlLib.ListViewCtrl.2 Control:
Part of malicious RTF file
The header of malicious RTF file looks like:
Header of malicious RTF file
Information from RTF Header (for more details visit):
ansicpg936 means it uses ANSI code page 936, (Simplified Chinese)
deflang1033 means the default language is 1033 (English, U.S.)
deflangfe2052 defines a far east/asian language (2052 = Chinese China)
Distribution
It spreads as an attachment by sending targeted phishing emails.
Technical Details
Payload
When the malicious RTF document is opened the exploit extracts an encoded file from its body. The exploit then decrypts the file using XOR with “0xDE”:
The malicious file before and after decrypting
After decryption it saves the file “msmx21.exe”, 5384 bytes in size, in the current user’s temporary folder:
%Temp%\msmx21.exe
The file is detected by Ad-Aware as Trojan.Win32.Generic!BT. It is a dropper that extracts other files from its body.
MD5: a332739ce42c74a8d8d8c63cdfbddd50
SHA1: 8fe449aa213a318aff2881a77ad138c2b3fbf03a
The dropper extracts the following file:
%Program Files%\Windows NT\svchost.exe
It is 542720 bytes, detected by Ad-Aware as Trojan.Win32.Generic!BT. The file loads other malicious programs into its address space.
MD5: 7c715101ec5c25470301c225fc8020d6
SHA1: 526a299249f902d5e6a61adb2a4fe2f121769e71
This file is stored in one of the following folders:
%ProgramFiles%\Windows NT
%ProgramFiles%\Windows NT\Accessories
%ProgramFiles%\Windows NT\Pinball
%ProgramFiles%\Windows Media Player
%ProgramFiles%\Web Publish
%ProgramFiles%\Outlook Express
%ProgramFiles%\Microsoft Office\Office10\Data
%ProgramFiles%\Microsoft Office\Office10
%ProgramFiles%\Microsoft Frontpage
%ProgramFiles%\Internet Explorer
%ProgramFiles%\ComPlus Applications
%CommonProgramFiles%\Microsoft Shared\MsInfo
%CommonProgramFiles%\Microsoft Shared\Office10
%CommonProgramFiles%\Proof
%CommonProgramFiles%\Web Folders
%CommonProgramFiles%\Web Server Extensions
%CommonProgramFiles%\System\ado
%CommonProgramFiles%\System\dao
%WinDir%\Help\Tours\mmTour
%WinDir%\Help\Tours\htmTour
%WinDir%\IME
%WinDir%\Installer
%WinDir%\Temp
%WinDir%\MsApps
%WinDir%\MsApps\MsInfo
%SystemDrive%\Documents and Settings\LocalService\Application Data\Microsoft
%SystemDrive%\Documents and Settings\LocalService\Local Settings\Application Data\Microsoft
%ALLUSERSPROFILE%\Application Data
%ALLUSERSPROFILE%\Application Data\Microsoft
%ALLUSERSPROFILE%\Application Data\Microsoft\Office
%ALLUSERSPROFILE%\Application Data\Microsoft\Office\Data
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows
%APPDATA%\Microsoft
%APPDATA%\Microsoft\Office
%APPDATA%\Microsoft\Office\Data
%APPDATA%\Microsoft\Windows
The dropper also extracts the following file:
%Program Files%\Windows NT\wsdktr.ltp
It is 74550 bytes, encrypted with RC4 streaming cypher with the key “dfdedkwe3322oeitodkdjeio3e9ekdjwasddcncmvjdasalwpeoryg7534hvn5wewse” and packed with Zlib. The file is a DLL (PE DLL-file), also packed with UPX.
MD5: 7e0760dcc466b4810a6ccc2767f00cc9
SHA1: 7cbf0c9540729b936f8141a684fc52c803ca0552
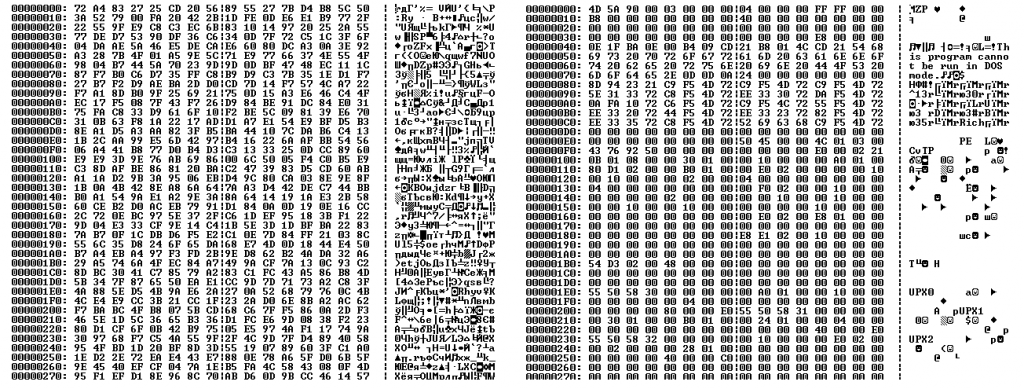
A fragment of memory dump with displaying the key
The malicious DLL before and after decrypting
To automatically run “%Program Files%\Windows NT\svchost.exe” each time Windows is booted, the following registry key is added:
[HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon] “Userinit” = “%Program Files%\Windows NT\svchost.exe ”All extracted files are marked as “hidden”.
Then the malware extracts a BAT script and saves it as “msc.bat” in the current user’s temporary folder:
%Temp%\msc.bat
The file contains the following code:
chcp 1251
Repeat
attrib -a -s -h -r “%Temp%\msmx21.exe”
del “%Temp%\msmx21.exe”
if exist “%Temp%\msmx21.exe” goto Repeat
del “%Temp%\msc.bat”
Once launched it modifies code page to 1251 (Cyrillic) and deletes extracted file “%Temp%\msmx21.exe” and itself.
With the help of “%Program Files%\Windows NT\svchost.exe ” attackers check the Internet connection by sending requests to the following websites:
www.microsoft.com
update.microsoft.com
If direct connection has not been established the malware retrieves proxy settings from Internet Explorer/Opera/Firefox and tries to connect again.
Once a connection is established, a DLL is decrypted from the file “%Program Files%\Windows NT\wsdktr.ltp”. It is then injected into “%Program Files%\Windows NT\svchost.exe ” address space. This DLL is a backdoor used to provide a remote connection to the infected computer.
The backdoor connects to the following C&C servers:
nt-windows-online.com
nt-windows-update.com
nt-windows-check.com
These servers were not in operation during this analysis.
Encrypted connection to “nt-windows-online.com”
Encrypted connection to “nt-windows-update.com”
Encrypted connection to “nt-windows-check.com”
Information about C&C servers obtained from WhoIs:
Domain Name: NT-WINDOWS-UPDATE.COM
Registrant:
Sergej Vereshhagin
ul.Mira 19 kv.39
Volgograd
Volgograd,400052
RU
Tel. +7.8442324390
Creation Date: 01-Apr-2011
Expiration Date: 01-Apr-2013
Domain name: nt-windows-online.com
Registrant:
Ustuygov Denis Egorovich
Organization: Ustuygov Denis
Address: Povorotnikova 19
City: Omsk
State: Omskaja obl.
ZIP: 644015
Country: RU
Phone: +7.3812557380
Fax: +7.3812557380
Creation date: 2011-04-01
Expiration date: 2013-04-01
Domain Name: NT-WINDOWS-CHECK.COM
Registrant:
Privat Person
Mihail Pyatinin
Nevskij prospekt, 176. kv.72
Saint Petersburg
Saint Petersburg,197341
RU
Tel. +7.8124585518
Creation Date: 04-Apr-2011
Expiration Date: 04-Apr-2013
Removal Recommendations
- Using Task Manager terminate the process (How to End a Process with the Task Manager):
%Program Files%\Windows NT\svchost.exe
- Delete the original malware file (its file name and location depends on the way the Trojan originally penetrated a user’s computer).
- Restore registry key values modified by the malware (How to Work with System Registry(“How to Work with System Registry“):
- Delete the file:
%Program Files%\Windows NT\svchost.exe
%Program Files%\Windows NT\wsdktr.ltp
- Clean the Temporary Internet Files folder, which contains infected files (“How to clean Temporary Internet Files folder“).
- Run a full scan of your computer using the Antivirus program with the updated definition database (“Download Ad-Aware Free“).