This post has been updated to add comments Linksys made online, which says company researchers couldn’t reproduce the information disclosure exploit on routers that installed a patch released in 2014. Representatives of Belkin, the company that acquired Linksys in 2013, didn’t respond to the request for comment that Ars sent on Monday. Ars saw the statement only after this article went live.
More than 20,000 Linksys wireless routers are regularly leaking full historic records of every device that has ever connected to them, including devices’ unique identifiers, names, and the operating systems they use. The data can be used by snoops or hackers in either targeted or opportunistic attacks.
Independent researcher Troy Mursch said the leak is the result of a flaw in almost three dozen models of Linksys routers. It took about 25 minutes for the Binary Edge search engine of Internet-connected devices to find 21,401 vulnerable devices on Friday. A scan earlier in the week found 25,617. They were leaking a total of 756,565 unique MAC addresses. Exploiting the flaw requires only a few lines of code that harvest every MAC address, device name, and operating system that has ever connected to each of them.
The flaw allows snoops or hackers to assemble disparate pieces of information that most people assume aren’t public. By combining a historical record of devices that have connected to a public IP addresses, marketers, abusive spouses, and investigators can track the movements of people they want to track. The disclosure can also be useful to hackers. The Shadowhammer group, for instance, recently infected as many as 1 million people after hacking the software update mechanism of computer maker ASUS. The hackers then used a list of about 600 MAC addresses of specific targets that, if infected, would receive advanced stages of the malware.
Got admin?
Besides handing out device information, vulnerable routers also leak whether their default administrative passwords have been changed. The scan Mursch performed earlier this week found about 4,000 of the vulnerable devices were still using the default password. The routers, he said, have remote access enabled by default and can’t be turned off as a workaround, because it’s required for an accompanying Linksys App to function.
That scenario makes it easy for hackers to quickly scan for devices that can be remotely taken over. Hackers can then obtain the Wi-Fi SSID password in plaintext, change DNS settings to send connected devices to malicious addresses, or carry out a range of other compromises. A recent attack group known as the BlackTech Group likely used similar router attacks to install the Plead backdoor on targeted computers.
Mursch told Ars that his tests show that devices are vulnerable even when their firewall is turned on. He also said that devices continue to leak even after running a patch Linksys issued in 2014.
Mursch said he disclosed the information leakage publicly after he privately reported it to Linksys officials and they closed the issue after determining it “Not applicable / Won’t fix.” Ars emailed press representatives of Belkin, the company that acquired Linksys in 2013, seeking comment earlier this week and never received a response.
In a statement published Tuesday, one day after Mursch’s post went live, Linksys representatives wrote:
Linksys responded to a vulnerability submission from Bad Packets on May 7th, 2019 regarding a potential sensitive information disclosure flaw: CVE-2014-8244 (which was fixed in 2014). We quickly tested the router models flagged by Bad Packets using the latest publicly available firmware (with default settings) and have not been able to reproduce CVE-2014-8244; meaning that it is not possible for a remote attacker to retrieve sensitive information via this technique. JNAP commands are only accessible to users connected to the router’s local network. We believe that the examples provided by Bad Packets are routers that are either using older versions of firmware or have manually disabled their firewalls. Customers are highly encouraged to update their routers to the latest available firmware and check their router security settings to ensure the firewall is enabled.
As mentioned above, Mursch said the 2014 patch failed to fix the vulnerability on the routers he tested, even when the firewall was turned on. The existence of 20,000 to 25,000 actively leaking routers suggest many people have either failed to apply the patch or that the patch doesn’t always work.
The list of vulnerable devices released by Mursch is here. An image is also below:
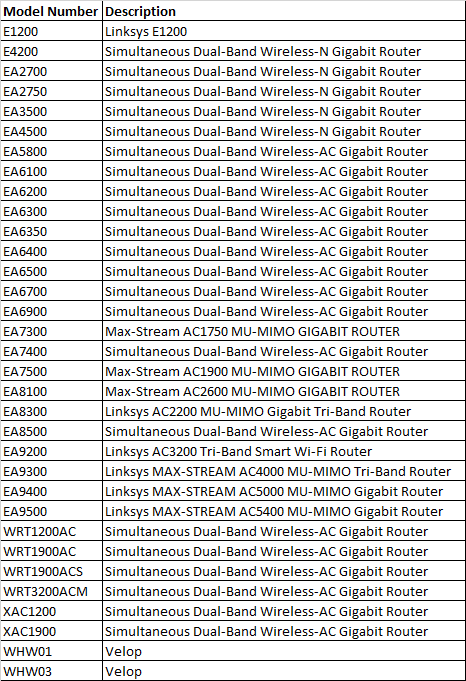
People using one of these devices would do well to test if it is leaking device history to the Internet even after installing the 2014 update. It is, users should either replace the router with a newer model or replace the Linksys firmware with a third-party offering such as OpenWrt.
via arstechnica.com