The National Institute of Standards and Technology (NIST) has released updated guidance on securing the supply chain against cyberattacks.
Since 2020, NIST has released two draft documents on how the enterprise can better defend itself from supply-chain attacks.
Today, in response to Executive Order 14028: Improving the Nation’s Cybersecurity, NIST has published ‘Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations‘ to provide guidance on identifying and responding to supply chain cybersecurity risks.
“Managing the cybersecurity of the supply chain is a need that is here to stay,” said NIST’s Jon Boyens, one of the publication’s authors. “If your agency or organization hasn’t started on it, this is a comprehensive tool that can take you from crawl to walk to run, and it can help you do so immediately.”
The document is a long read, weighing in at 326 pages, but includes valuable information on supply chain risks, from evaluating foreign control over a software/product’s development to risks associated with using external IT service providers.
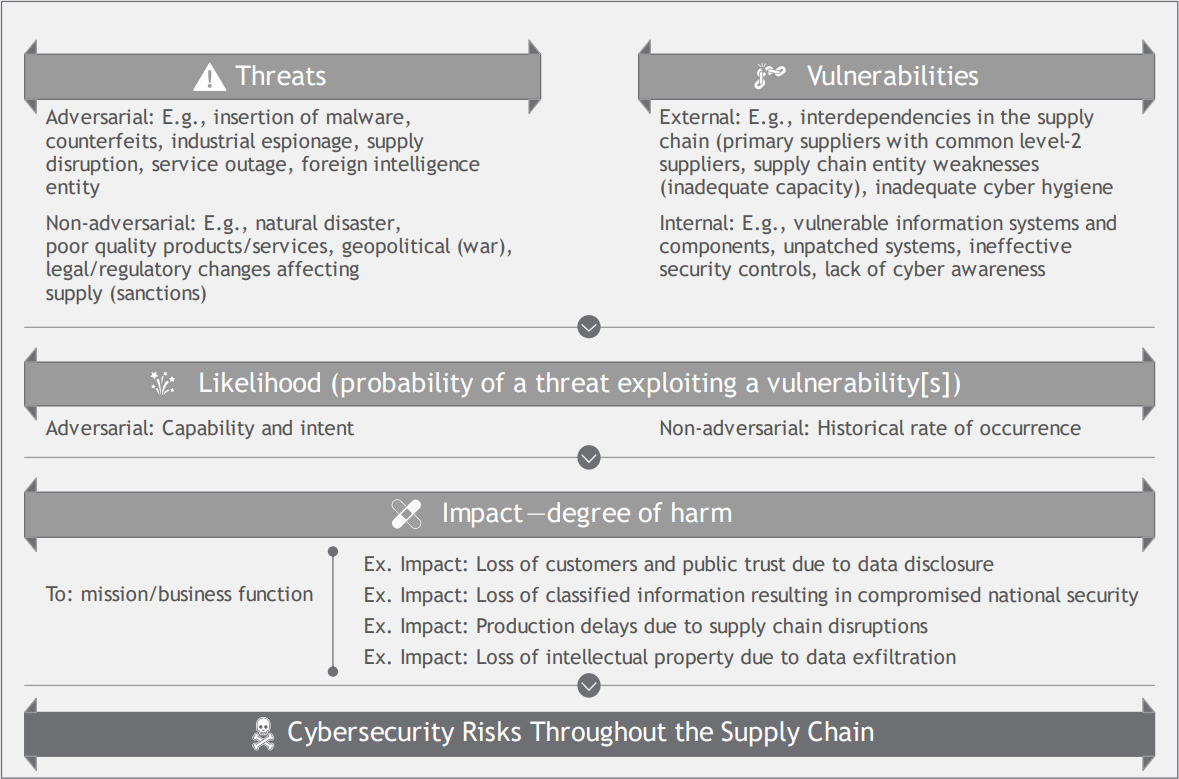
Source: NIST
“It has to do with trust and confidence,” said NIST’s Angela Smith, an information security specialist and another of the publication’s authors. “Organizations need to have greater assurance that what they are purchasing and using is trustworthy. This new guidance can help you understand what risks to look for and what actions to consider taking in response.”
Due to the length and complexity of the document, NIST plans on releasing a quick-start guide to help organizations who are just starting their C-SCRM (Cybersecurity Supply Chain Risk Management) endeavors.
Supply-chain attacks are becoming increasingly popular targets for threat actors, as it allows them to compromise a single product and have it impact numerous downstream companies who utilize it.
The severity of supply-chain attacks was demonstrated in real-world scenarios when threat actors compromised SolarWinds to infect downstream customers, Kaseya’s MSP software was used to encrypt over a thousand companies, and how npm modules were used to execute remote commands.
These attacks had widespread consequences for many organizations simply by compromising a single source, illustrating the need for the enterprise to add safeguards against supply-chain attacks.
via www.bleepingcomputer.com


