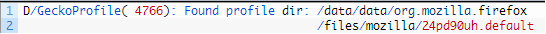
/data/data/org.mozilla.firefox/files/mozilla/<RANDOM-STRING>.default.
Where the random name for user’s profile is used to prevent unwanted access to this directory in case of Firefox exploitation.
Downloaded files with the exploit code will be saved automatically to the SD card at location/mnt/sdcard/Download, that can be read by the attacker using any malicious Android app.
REPORTED VULNERABITIES
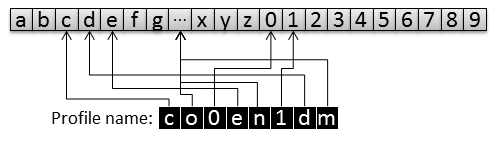
1.) Profile Directory Name Weak Randomization (CVE-2014-1516) – The Attacker who knows the seed of the Pseudo-Random Number Generator (PRNG) can easily predict its output and eventually the generated Firefox Profile name.
2.) Profile Directory Name Leaks to Android System Log (CVE-2014-1484) – Android operating system writes the randomly generated Firefox user’s Profile Directory Name in the Android System Log (logcat) at various locations, that can be used to steal private information.
In Android version 4.0 and below, installed apps with READ_LOGS permission can easily read Android system logs to identify the name of the Firefox user profile folder.
3.) Automatic File Download to SD Card (CVE-2014-1515) – Firefox for Android will download any file automatically to the SD card, if not of any known extension. Malicious apps with READ_EXTERNAL_STORAGE permission can read files from the SD card to extract non-renderable data such as the cookies database.
4.) Crash Reporter File Manipulation (CVE-2014-1506) – In cases where the application crashes, Firefox sends the crash dumps located in /data/data/org.mozilla.firefox/files/mozilla/Crash Reports/pending on the device file system. Using the exploit, an attacker can manipulate the crash report file path to the Android Log file in order to steal it. Researchers have also explained second way to hack user data using this vulnerability.
RESEARCH PAPER:
via http://thehackernews.com/