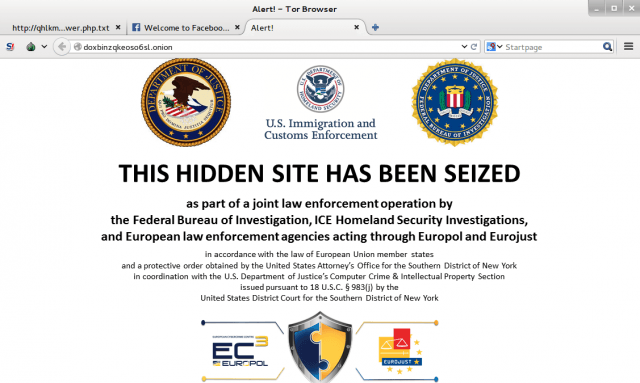
Last week’s takedown of Silk Road 2.0 wasn’t the only law enforcement strike on “darknet” illicit websites being concealed by the Tor Project’s network of anonymizing routers. A total of 410 .onion pages on at least 27 different sites, some of which sell everything from drugs to murder-for-hire assassins, were shut down as part of Operation Onymous—a joint operation between16 member nations of Europol, the FBI, and US Immigration and Customs Enforcement.
While 17 arrests were made, some operators of sites taken down by the worldwide sweep remain at large. One of them—the co-operator of Doxbin, a site that allowed others to post personal identifying information frequently used for intimidation, identity theft, or other malicious purposes—has shared details of his site’s takedown with Tor developers in hopes they’ll find ways to protect other users of the network. An apparent distributed denial of service (DDoS) attack against Doxbin may have been used to uncover its actual location, and the same approach may have been used to expose other darknet servers seized by law enforcement.
Log files shared by the Doxbin proprietor, who calls himself nachash, suggest that sites may have been “decloaked” using Web requests intentionally crafted to break Tor’s Hidden Services Protocol. It’s also possible that his site was given up by bad PHP code. In a series of e-mails to the tor-dev list entitled “yes, hello, Internet supervillain here,” nachash said that his server—a virtual private server running the German hosting service Hetzner—was initially hit by what he believed was a denial of service attack in August.
Update: The operator of Doxbin sent an update on Sunday evening to Tor developers, saying that at least part of what he reported as a denial of service attack earlier was in fact someone crawling his website. However, the crawler was not involved in the malformed traffic sent later.
From August 21 to August 28, the logs show a wave of requests that include text proceeded by %5C%22—which in PHP requests would be parsed as a quotation mark by PHP code. Trailing the “escaped” quote, the requests include what appear to be URLs for websites such as Twitter and Hack Forums. However, those websites were actually loaded with fake subdirectories such as “/old/code/fail”:
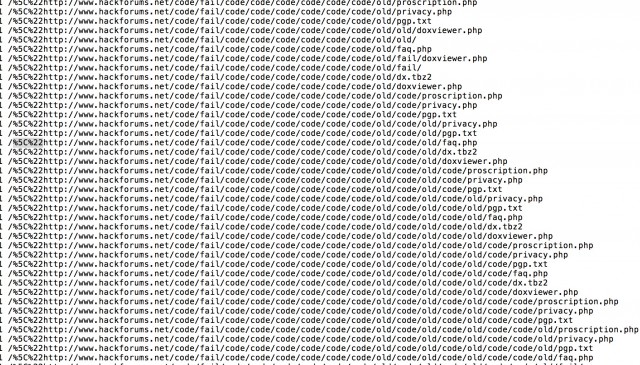
The requests pushed the traffic for the service up to about 1.7 million page requests for August—nearly three times the normal traffic load for the site. A month later, the same pattern began again, and nachash said that he started redirecting those requests to another Tor hidden service site (the Hidden Wiki’s “Hard Candy” page, a directory of child pornography sites). “I also added a grip -v”—the “invert match” feature for the GNU grep command, which excludes a specific pattern from output—“to my log report script in order to filter out the noise,” nachash wrote. “[this was] possibly a mistake, but we both tailed logs and watched for something like a different attack style that the DDoS was being used to cover and never noticed anything.” Eventually the requests trailed off from a peak of five requests per second down to one every three to six seconds. Ultimately, the requests stopped entirely.
The theory posited by “the kid who started Doxbin“ to nachash was that the attack was an attempt to force connections to the site’s various .onion addresses to follow paths that went over Tor network nodes set up by law enforcement. By filling up the “circuits” through secure Tor network nodes, law enforcement operatives could have made it possible to connect to the services only through Tor routing servers they controlled—allowing them to see the real Internet Protocol address of the server hosting them.
Doxbin went down on November 6, the same day that Silk Road 2.0 was seized. At or before 1 PM UTC, nachash wrote:
“I checked the most current Doxbin onion and attempted to ssh into the box every couple of hours for around the first 24 hours, until a friend pointed out that one of the old Doxbin onions was serving up the Silk Road 2.0 seizure page. At the time, the main onion was serving up some 404 page (Which I expected to eventually point to some sort of honeypot, but the pigs really let me down on that one), while other onions were unresponsive. This had changed by the next day, when all the onions from the Doxbin box were pointed to the seizure page. The speculation has been that the cops were adding onions one at a time, and my personal experience supports that. Police who are dedicated to seizing and taking control of hidden services are still struggling with managing a torrc file [the Tor service configuration file] efficiently. Go figure.
While no tears may be shed over sites like Silk Road 2.0 and Doxbin, the implications for other hidden services—and for users of the Tor network in general—are unnerving. If it’s possible for government actors to use denial-of-service attacks to force Tor traffic over connections that are owned and operated by them, it could present privacy problems for anonymized sites used by whistle-blowers, political activists and dissidents, journalists, and others trying to avoid the eyes of oppressive regimes.
via arstechnica.com