Researchers have uncovered a group of Wall Street-savvy hackers that has penetrated the e-mail accounts of more than 100 companies, a feat that has allowed them to obtain highly valuable plans concerning corporate acquisitions and other insider information.
FIN4, as the group is known, relies on a set of extremely simple tactics that in many cases has allowed them to remain undetected since at least the middle of 2013, according to a report published Monday from security firm FireEye. Members boast a strong command of the English language and knowledge of corporate finance and Fortune 500 culture. They use that savvy to send highly targeted spearphishing e-mails that harvest login credentials for Microsoft Outlook accounts. The group then uses compromised accounts of one employee, customer, or partner to send spearphishing e-mails to other company insiders. At times, the attackers will inject a malicious message into an ongoing e-mail discussion among multiple people, furthering their chances of success.
E-mails are sent from the accounts of people the target knows, and they discuss mergers, acquisitions, or other topics already in progress. The attackers often bcc other recipients to make it more difficult to detect the malicious e-mail. The messages appear to be written by native English speakers and often contain previously exchanged Microsoft Office documents that embed hidden malicious macros. This results in fraudulent e-mails that are extremely hard to detect, even by some people who have been trained to spot such phishing campaigns. Witness the following:
Subject: employee making negative comments about you and the company
From: [name]@[compromised company’s domain]
I noticed that a user named FinanceBull82 (claiming to be an employee) in an investment discussion forum posted some negative comments about the company in general (executive compensation mainly) and you in specific (overpaid and incompetent). He gave detailed instances of his disagreements, and in doing so, may have unwittingly divulged confidential company information regarding pending transactions. I am a longtime client and I do not think that this will bode well for future business. The post generated quite a few replies, most of them agreeing with the negative statements. While I understand that the employee has the right to his opinion, perhaps he should have vented his frustrations through the appropriate channels before making his post. The link to the post is located here (it is the second one in the thread):
http://forum./redirect. php?url=http://%2fforum%2fequities%2f375823902%2farticle.php\par
Could you please talk to him?
Thank you for the assistance,
[name]
FireEye researchers said FIN4 members have compromised the accounts of C-level executives, legal counsel, regulatory and compliance personnel, scientists, and advisors of more than 100 companies. About 80 of them are publicly traded companies, while the remaining 20 are Wall Street firms that advise corporations on legal or securities matters or possible or pending mergers and acquisitions. As a result, the group stood to make a windfall if it used the insider information to buy or sell stocks before the information became widely known.
“Our visibility into FIN4’s activities is limited to their network operations,” FireEye researchers Barry Vengerik, Kristen Dennesen, Jordan Berry, and Jonathan Wrolstad wrote. “We can only surmise how they may be using and potentially benefiting from the valuable information they are able to obtain. However one fact remains clear: access to insider information that could make or break stock prices for dozens of publicly traded companies could surely put FIN4 at a considerable trading advantage.”
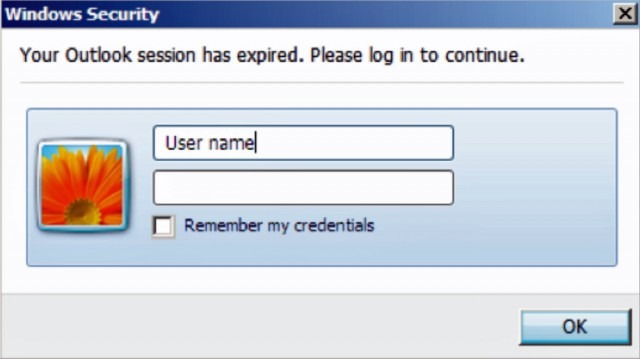
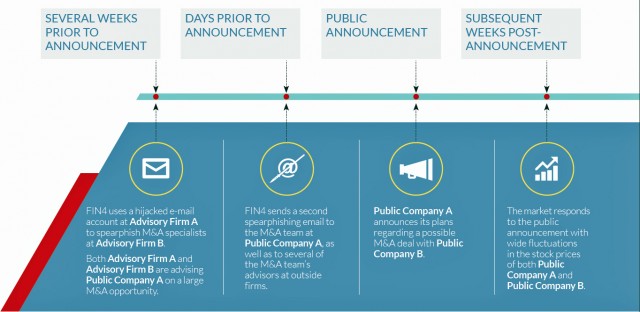
Embedded in the previously stolen documents are Visual Basic Applications (VBA) macros that prompt readers to enter the Outlook user names and passwords. The scripts then funnel the credentials to servers controlled by the attackers. In other, earlier cases, the spearphishing e-mails contained links to fake Outlook Web App login pages that prompted visitors to enter their passwords. Some of the attacks FireEye observed targeted multiple parties inside law firms, consultancies, and corporations as they discussed particular pending business deals. In one instance, attackers used previously acquired access to e-mail accounts at an advisory firm to harvest information being exchanged about an acquisition under consideration involving one of its clients. The attackers used a compromised account belonging to the advisory firm to compromise the company, which FireEye identified only as Public Company A.
“After news of the possible acquisition was made public, Public Company A’s stock price varied significantly,” Monday’s report stated. “It is likely the FIN4 used the inside information they had to capitalize on these stock fluctuations.”
Many phishing campaigns are relatively easy to spot because the e-mail lures contain grammatical errors or embed malicious files that are readily detected by most antivirus. The FIN4 operations, by contrast, are notable for their organization, persistence, and familiarity of the organizations being targeted. In many respects, the operation resembles those of so-called advanced persistent threats (APTs) in which government-allied hackers case the networks of corporations, government agencies, and non-governmental organizations. Cyber criminals’ embrace of APT tactics and techniques in financially motivated online criminal activity is one of the trends researchers from fellow security firmKaspersky Lab expect to see increase in the coming year.
The FIN4 campaigns were ongoing at the time Monday’s report was being written. FireEye recommends firms protect themselves by disabling the execution of VBA scripts unless there is a strong need for them. FireEye also recommends administrators monitor their networks for computers that connect to TOR servers, since that’s another way attackers attempt to cover their tracks. Additionally, admins can check to see if employees have connected to any one of nine Internet domains known to be used to funnel insider information. Of course, the best thing any potential target can do is to educate employees how to spot phishing attacks. The FIN4 attackers have just raised the bar, so chances are most education programs should be revised to help employees spot these new and improved tactics.
via arstechnica.com