The Distributed Denial of Service (DDoS) attack is becoming more sophisticated and complex with the increase in the skills of attackers and so, has become one of favorite weapon for the cyber criminals to temporarily suspend or crash the services of a host connected to the Internet and till now nearly every big site had been a victim of this attack.
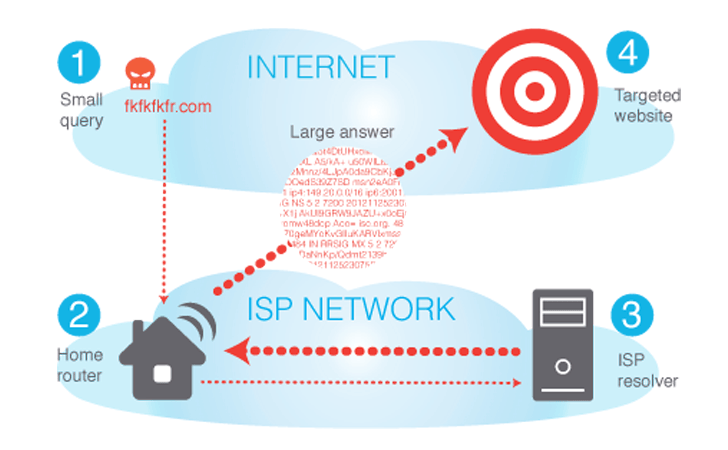
Since 2013, Hackers have adopted new tactics to boost the sizes of Distributed Denial of Service (DDoS) attack known as ‘Amplification Attack’, leveraging the weakness in the UDP protocols. One of the commonly used by hacker is (Domain Name System) DNS Reflection Denial of Service (DrDoS).
WHAT IS DrDoS ATTACK?
The DNS Reflection Denial of Service (DrDoS) technique exploits security weaknesses in the Domain Name System (DNS) Internet protocol. Using Internet protocol spoofing, the source address is set to that of the targeted victim, which means all the replies will go to the target and the target of the attack receives replies from all the DNS servers that are used. This type of attack makes it very difficult to identify the malicious sources.
MILLIONS OF HIJACKED-ROUTERS AIDING DrDoS ATTACKS
The new research carried out by DNS providers Nominum, provides ISPs with DNS based analytics and monetization solutions, revealed that the DNS-based DDoS amplification attacks have significantly increased in the recent months and hackers are using home as well as small office routers to amplify the bandwidth.
The report claimed that more than 24 million home routers, majority of which (800,000 routers) located in the UK are vulnerable to various firmware flaws, that allow hackers to gain unauthorised access and modifying DNS (Domain Name Server) settings.In a previous report, we also disclosed that more than 200,000 Algerian TP-LINK Routers are vulnerable to Hackers, allowing them to hijack DNS requests.
This could be exposing ISPs and their users to participate in the massive Internet DNS-based Distributed Denial of Service (DDoS) attacks unknowingly.
In February alone, more than five million home routers were used to generate DDoS attack traffic, and in January, more than 70% of total DNS traffic on a provider’s network was associated with DNS amplification.
The impact on Internet service providers (ISPs) is four times because amplification attacks generates malicious traffic that not only consume bandwidth, but also cause support costs and impact the reputation of the ISPs, Nominum said.
“Existing in-place DDoS defenses do not work against today’s amplification attacks, which can be launched by any criminal who wants to achieve maximum damage with minimum effort,” explained Sanjay Kapoor, CMO and SVP of Strategy, Nominum. “Even if ISPs employ best practices to protect their networks, they can still become victims, thanks to the inherent vulnerability in open DNS proxies.”
“ISPs today need more effective protections built-in to DNS servers. Modern DNS servers can precisely target attack traffic without impacting any legitimate DNS traffic. ThreatAvert combined with ‘best in class’ GIX portfolio overcomes gaps in DDoS defenses, enabling ISPs to constantly adapt as attackers change their exploits, and precision policies surgically remove malicious traffic.”
WHY DrDoS?
The main reason of the increase in the popularity of DNS amplification or DrDoS attacks is that it requires little skills and efforts to cause major damage. The high attack bandwidth is made possible only as the attackers are using misconfigured domain-name service (DNS) servers known as open recursive resolvers or open recursors to amplify a much smaller attack into a larger data flood.
“Because vulnerable home routers mask the target of an attack it is difficult for ISPs to determine the ultimate destination and recipient of huge waves of amplified traffic,” said Nominum.
RISE IN MASSIVE DDoS ATTACKS
The DDoS techniques have massively increased with the attackers becoming more skillful at working around the network security. A Year back, a massive 300Gbps DDoS attack launched against Spamhaus website that almost broke the Internet. Also earlier this year, hackers have succeeded in reaching new heights of the massive DDoS attack targeting content-delivery and anti-DDoS protection firm CloudFlare, reaching more than 400Gbps at its peak of traffic, striking at the company’s data servers in Europe.
At the beginning of last month, the US-CERT also issued an alert warning, listed certain UDP protocols identified as potential attack vectors for Amplification Attack, including DNS, NTP, SNMPv2, NetBIOS, SSDP ,CharGEN, QOTD, BitTorrent, Kad, Quake Network and Protocol Steam Protocol.Users are recommended to change the default username and password of their routers and ensure that you have updated router firmware installed with security patches. You router should be accessible only from the local network or LAN.
via http://thehackernews.com/