Details have been released for an attack that allows a hacker to execute arbitrary code without user interaction on macOS systems.
The researcher that made the discovery claims that the vulnerability is unpatched and works on macOS Mojave 10.14.5 and below.
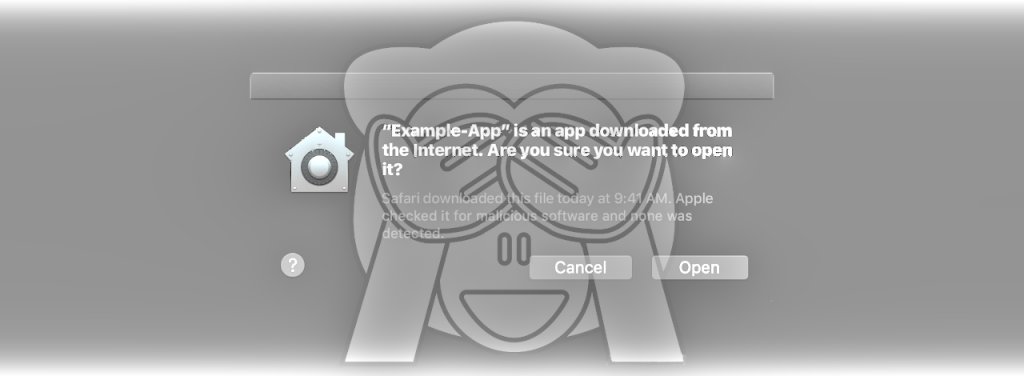
By leveraging the flaw it is possible to bypass Gatekeeper, the built-in defense in macOS that guards the operating system against untrusted applications. Gatekeeper achieves this by verifying the code signing certificate obtained through Apple’s developer program.
Abusing legitimate features
According to details from Filippo Cavallarin of cyber security company Segment in Italy, Gatekeeper treating external drives and networks as safe locations can be combined with other legitimate features on macOS to execute untrusted apps without warning the user.
He says that combining the OS’s automount functionality with the support for symbolic links it is possible to run untrusted code without triggering a reaction from Gatekeeper. On macOS, a user can automatically mount network shares using the ‘autofs’ command.
Another feature helping the attack discovered by Cavallarin is the support for symbolic links that can point to a location on the network. Symbolic links in archives are not verified so users can be tricked to click them and access a remote share.
The researcher published the complete details for the attack and a video demonstrating the validity of his findings:
To better understand how this exploit works, let’s consider the following scenario:
1. An attacker crafts a zip file containing a symbolic link to an automount endpoint she/he controls (ex Documents -> /net/evil.com/Documents) and sends it to the victim.
2. The victim downloads the malicious archive, extracts it and follows the symlink
In this context, the victim accesses code from a location that is controlled by the attacker and trusted implicitly by Gatekeeper. Executing an app this way does not trigger the security mechanism in macOS.
Furthermore, Cavallarin says that because Finder is designed to hide app extensions and the full path from the title bar, users would have a hard time spotting the attack. However, a hacker would first need access to the network to pull off this attack, which may not go undetected.
A potential solution for this issue is to disable automatic mounting of network shares by following the steps below:
1. Edit /etc/auto_master as root
2. Comment the line beginning with '/net'
3. RebootCavallarin claims he informed Apple of the issue on February 22 and that the company should have fixed it with the security updates in May. The researcher says that the issue is still there and that “Apple started dropping my emails.”
“Since Apple is aware of my 90 days disclosure deadline, I make this information public,” the researcher says.
In this month’s security updates for macOS, Apple released a patch for an issue – tracked as CVE-2019-8589, that allowed a malicious application to bypass Gatekeeper. The fix is available for macOS Mojave 10.14.4, though.
BleepingComputer was not able to confirm the validity of the attack described by Cavallarin and the researcher did not return a request but the details he provided seem to fit the bill. The Gatekeeper bypass technique is present in MITRE’s catalog of adversary tactics and techniques:
In macOS and OS X, when applications or programs are downloaded from the internet, there is a special attribute set on the file called com.apple.quarantine. This attribute is read by Apple’s Gatekeeper defense program at execution time and provides a prompt to the user to allow or deny execution.
Apps loaded onto the system from USB flash drive, optical disk, external hard drive, or even from a drive shared over the local network won’t set this flag. Additionally, other utilities or events like drive-by downloads don’t necessarily set it either. This completely bypasses the built-in Gatekeeper check.
via www.bleepingcomputer.com