Android smartphones from multiple vendors, including Samsung, Huawei, LG, and Sony are susceptible to an advanced type attack that can alter device settings via a short text message.
Bad actors can leverage the weakness to send notifications seemingly from the mobile carrier and trick users into accepting what looks like network-specific configuration. This could instruct the device to route traffic through a malicious proxy.
Mobile carriers can deliver messages to a client terminal via the Open Mobile Alliance Client Provisioning (OMA CP) protocol. It uses over-the-air (OTA) communication and requires minimum interaction from the recipient.
Specification issue
Researchers at Check Point found that a mobile operator’s (OTA) provisioning process lacks a strong authentication mechanism that would validate messages coming from the network operator and not an unauthorized party.
In second-generation cellular technology (2G), for instance, there is no mutual authentication between the terminal and the network; only the phone needs to do this, while the operator is not required to authenticate to the terminal.
This threat does not depend on the type of cellular network, though. Slava Makkaveev, one of the researchers investigating the problem, told BleepingComputer that this is a specification issue in the OMA CP protocol, which allows sending provisioning messages without authentication.
If an authentication mechanism is present, it is based on the International Mobile Subscriber Identity (IMSI) number, which is unique for every user of a cellular network.
Popular phone brands susceptible
The researchers discovered that phones from Samsung, Huawei, LG, and Sony, which combined cover more than 50% of the Android phone market, can receive malicious settings through weakly-authenticated provisioning messages. “Samsung phones compound this by allowing unauthenticated OMA CP messages as well,” the researchers say in a report released today.
To run an attack, the threat actor would need a GSM modem (priced around $10) or a phone running in modem mode to send binary messages, and a simple script to compose thee OMA CP.
OTA provisioning messages can be used to change the following settings on the phone:
• MMS message server
• MMS message server
• Proxy address
• Browser homepage and bookmarks
• Mail server
• Directory servers for synchronizing contacts and calendar
Attackers targeting Samsung phones can send the malicious messages without needing to authenticate. If users accept the CP, the phones settings will be modified.
For other phones, an attacker would need the International Mobile Subscriber Identity (IMSI) numbers of the potential victims to deploy the same attack as in the case of Samsung phone users. Sevearal methods exist to obtain the IMSI number.
The researchers say that OMA CP messages have an optional security header for validating the provisioning message. This needs to be authenticated with the IMSI number.
This check, though, does not help the user in any way since they will not see any details that would identify the sender.
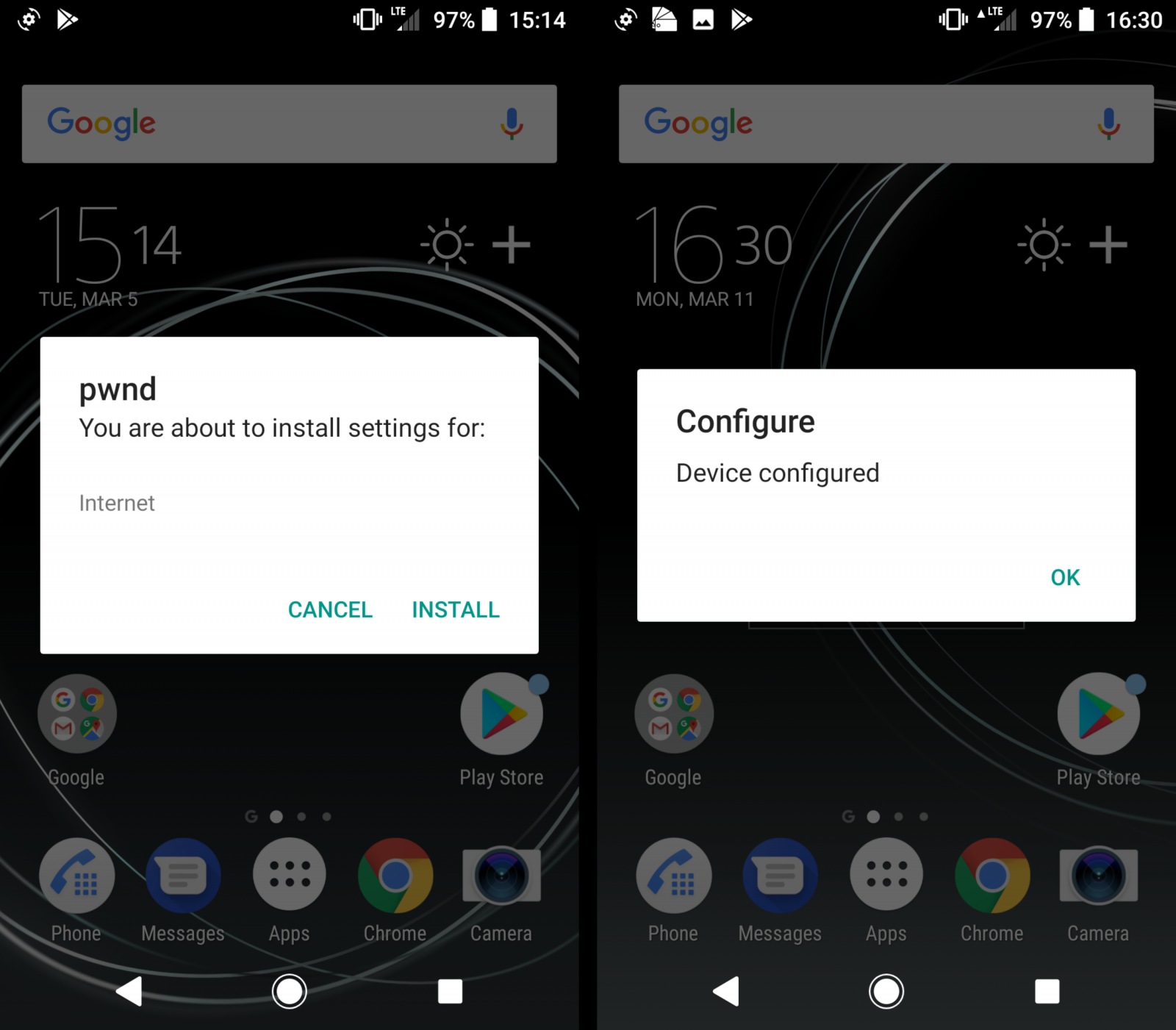
Alternatively, if the IMSI number cannot be obtained, the attacker has another way to deploy the attack, but it involves sending two messages to the victim.
“The first is a text message that purports to be from the victim’s network operator, asking him to accept a PIN-protected OMA CP, and specifying the PIN as an arbitrary four-digit number. Next, the attacker sends him an OMA CP message authenticated with the same PIN. Such CP can be installed regardless of the IMSI, provided that the victim accepts the CP and enters the correct PIN.”
Not all vendors released a patch
Check Point in March informed the vendors impacted by this attack of the vulnerability. Samsung and LG already rolled out an appropriate fix.
Huawei devices continue to be susceptible to the attack as the company plans to patch the weakness in the next generation of Mate or P series of its smartphones.
Sony did not acknowledge the flaw, motivating that their products follow the OMA CP specification.
via www.bleepingcomputer.com