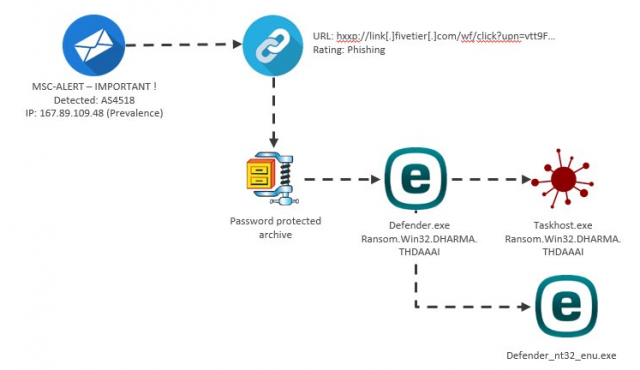
A new Dharma ransomware strain is using ESET AV Remover installations as a “smoke screen” technique designed to distract victims while their files are encrypted in the background as detailed by Trend Micro.
The ransomware is pushed by the attackers on their targets’ computers using a spam campaign which delivers email attachments containing a Dharma dropper binary packed as a password-protected self-extracting archive named Defender.exe and hosted on the hacked server of link[.]fivetier[.]com.
The password for the malicious attachment is listed in the spam email, a technique designed to incentives curios victims to open the archive and inadvertently launch the Dharma-infected executable on their system.
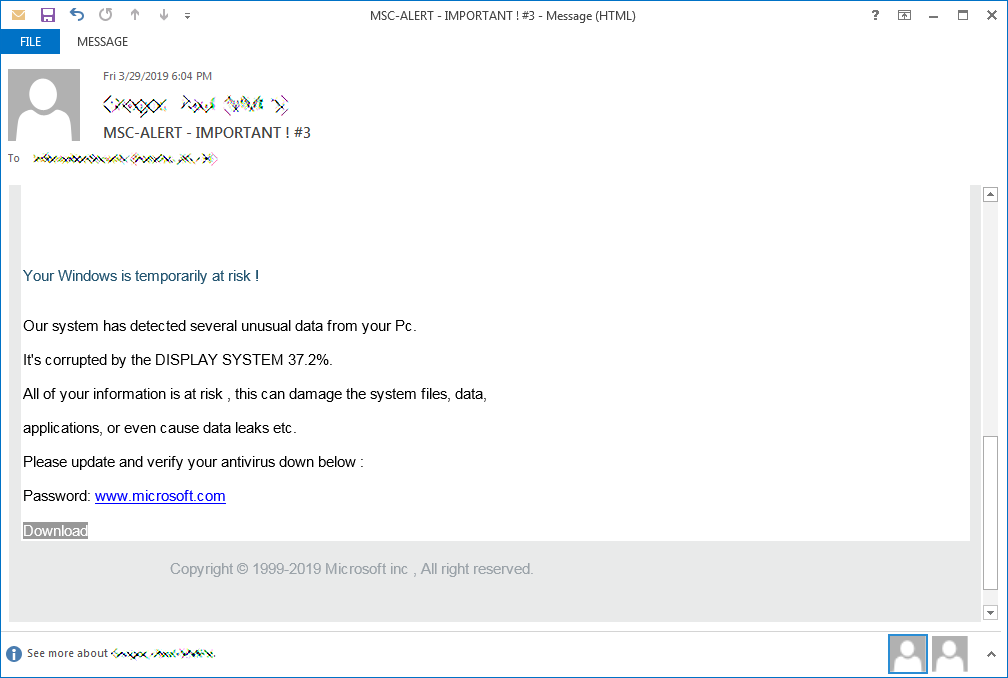
The full contents of such a spam email are listed below:
Your Windows is temporarily at risk !
Our system has detected several unusual data from your Pc.
It's corrupted by the DISPLAY SYSTEM 37.2%.
All of your information is at risk , this can damage the system files, data,
applications, or even cause data leaks etc.
Please update and verify your antivirus down below :
Password: www.microsoft.com
DownloadOnce Defender.exe is executed, it will drop on the system an old ESET AV Remover installer named Defender_nt32_enu.exe, and a taskhost.exe Dharma binary added to C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\ which gets launched and starts encrypting the victim’s hard drives.
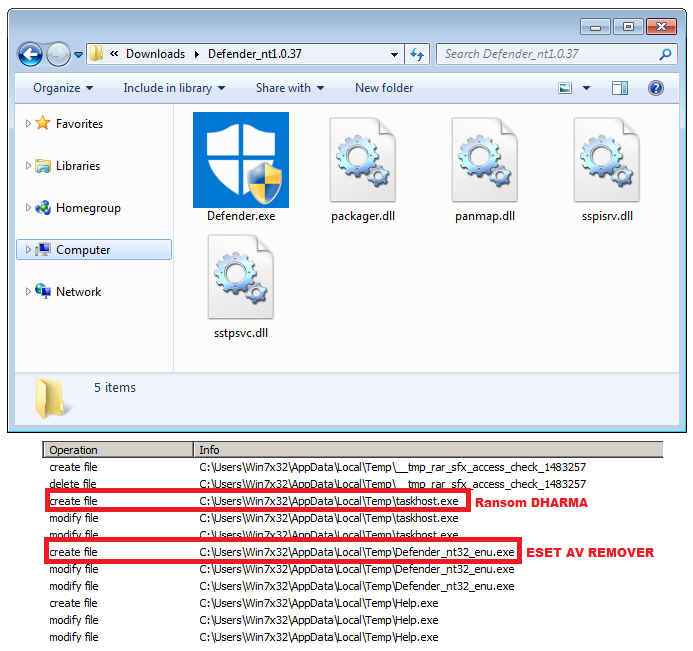
The ESET AV Remover installer will automatically be launched after the self-extracting archive is executed, attracting the victim’s attention while the Dharma ransomware encrypts the contents of the hard drive in the background.
Tests conducted by BleepingComputer show that this ransomware campaign is installing a Dharma variant that appends the ETH extension to encrypted file names.
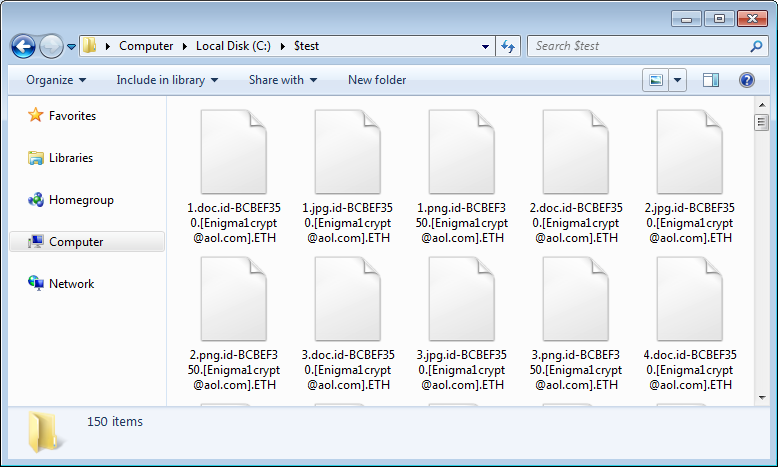
It also uses the Enigma1crypt@aol.com email address as a way to contact the ransomware developer.
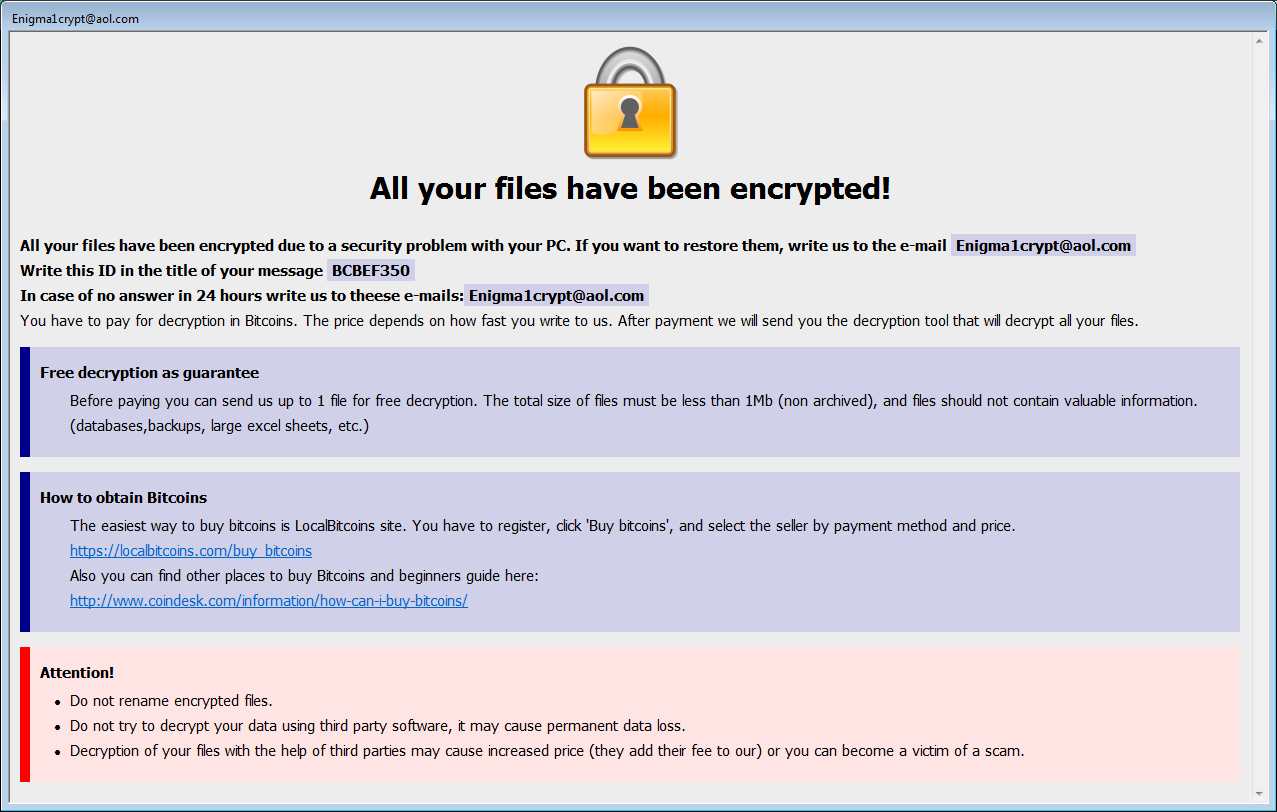
As Trend Micro says in their analysis of this new Dharma behavior, “the ransomware will still encrypt files even if the installation is not started. The malware runs on a different instance than the software installation, so their behavior is not related.”
Additionally, “The ransomware will run even if the tool installation is not triggered, and the tool can be installed even if the ransomware does not run. The installation process seems included just to trick users into thinking no malicious activity is going on.”
Given that the ESET AV Remover is legitimate software signed with a valid ESET digital signature on June 22, 2017, by bundling it together with their malware the attackers are trying to pull a “magic trick” designed to divert the victims focus, keeping them busy and their attention directed at something else while Dharma quickly renders the data on their hard drives unusable.
Following the report sent by Trend Micro before their analysis was published, ESET issued the following statement:
The article describes the well-known practice for malware to be bundled with legitimate application(s). In the specific case Trend Micro is documenting, an official and unmodified ESET AV Remover was used. However, any other application could be used this way. The main reason is to distract the user, this application is used as a decoy application. ESET threat detection engineers have seen several cases of ransomware packed in self-extract package together with some clean files or hack/keygen/crack recently. So this is nothing new.
In the specific case described by Trend Micro, the ransomware is executed right after our remover application, but the remover has a dialogue and waits for user interaction, so there is no chance to remove any AV solution before the ransomware is fully executed.
Trend Micro provides a list of indicators of compromise (IOCs) that can be used to detect and block attacks using this Dharma ransomware strain at the end of their report.
via www.bleepingcomputer.com